Setting up a secure home network for remote access
I was recently forced to relocate for work at a very short notice so I had to move with bare minimal belongings and rent a room in Denver. I left behind my gaming/editing PC and all of my SSDs at home in Virginia so I wanted a solution that allows me access to my project files, photos, movies, TV series etc. remotely.
I approached this “project” wearing a customer success manager hat, as I would at work, by first listing the requirements as stories –
Note: Local site refers to my home in Virginia, office refers to my workplace in Colorado and remote apartment refers to my temporary accommodation in Colorado
As a user, I must have all my files and media in one redundant storage location
As a user, I must have secure access to all my project files from my remote apartment, office and the local site on devices which have aVPN client installed
As a user, I must be able to upload new files to the redundant storage from remote and local locations
As a user, I would like to stream movies and view the photos library from the smart TV at the local site
As a user, I would like to have non-VPN, limited yet secure access to files via a browser when away from remote sites, such as in a coffee shop on devices which doesn’t have VPN clients installed
As a system admin, I would like an easy-to-manage redundant storage, preferable with a suitable prebuilt firewall solution and an automated backup to cloud solution
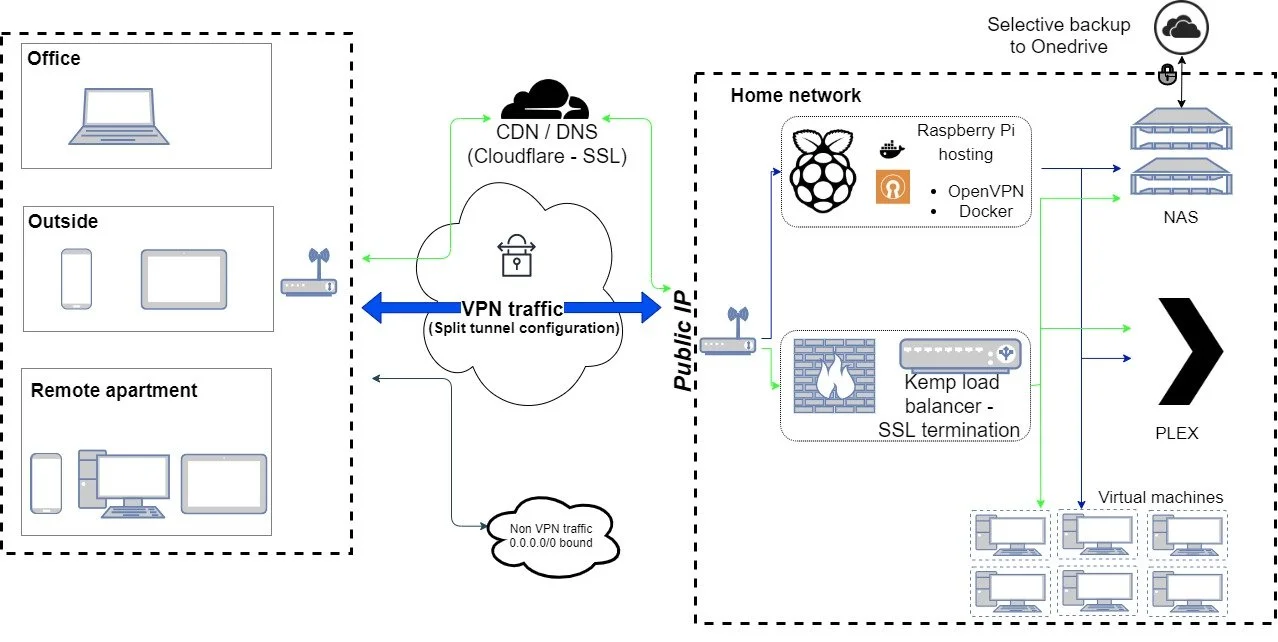
I did a quick mockup of the set up using draw.io (refer to diagram below) to get an idea of the components that I would need, and the cost involved. I had an initial determination of the total budget beforehand so that I could choose the equipment and other components of the setup accordingly. The goal, in my case, was not to focus on future proofing the set up but rather on cost optimization. Therefore, for the hardware, I used equipment such as switches, RJ45 cables, routers and old laptops that I already had lying around. On the software side, my choices were either open source or commercial software that offered a free plan.
Mock up of the remote access set up. The green arrows indicate non-vpn based access, the blue arrows indicate vpn based traffic and the black arrow include general internet access which doesn’t involve the home network
Next let’s take a look at the choices that I made for some of the key components in the setup:
Network Attached Storage (NAS) – Lets start things off from one of the most critical component, which glues the whole setup together, the NAS. I picked up a Synology NAS based on the unanimous recommendations from the good folks on the internet. Synology stands out simply because of their mature software, a clean GUI, and third-party app support. Two Seagate hard disks are installed in the NAS with RAID 1 configuration for redundancy.
VPN server – I used a Raspberry 4 with 8 GBs of ram for the VPN server. The horsepower on this tiny PC is plenty for traffic and workloads that I anticipate. As for the software, instead of configuring OpenVPN on the default distro, Raspbian, I decided to go with PiVPN, which has a simple step-by-step set up process to easily get an OpenVPN server going. I created only the bare minimum number of client certificates for security purposes but just enough so as to not share certificates among clients.
DNS provider – I chose Cloudflare over route 53 for two reasons. First - There was $0 fee for managing one domain in Cloudflare compared to the $0.50/month fee in AWS. Second – Cloudflare provides a free signed certificate to be used for SSL/TLS end- to-end encryption with my domain. This allows encrypted https communication between my devices and my servers (NAS and PLEX). Finally, using a dns provider such as Cloudflare (or AWS route 51) hides your public IP which provides an add layer of security.
Load balancer – I incorporated a load balancer into the setup not because I foresee large volumes of traffic but rather for security reasons. With a load balancer in the mix, you only open up one port in your router for port forwarding purposes. The load balancer will then take care of redirecting your request and traffic to the origin servers based on rules that I’ve defined. The SSL termination can also be done in the load balancer which is very convenient to setup and places less load on the origin servers. I choose Kemp as the load balancer as it had a very generous free plan. Kemp was installed on a spare laptop instead of on the Pi to eliminate a single point of failure.
Streaming media server – the choice here was quite simple given the immense popularity of the Plex server. Plex was configured to point to a separate volume in my NAS, which contained all of my movies, TV series and photos. The media can therefore be either streamed from a smart TV/smart phone (https traffic) or accessed as files from a mounted volume on a Windows device (via the VPN tunnel)
Cloud backup – I already own an Office 365 subscription, which includes Onedrive, so here again the choice was already made for me. Synology has a native app, which makes setting up online backup easy so I only had to choose the folders which I wanted synced up to the cloud and everything was good to go.
Virtual machines – I was already running few virtual machines, which I use for some of my projects. As I was already using vmware for ths purpose and had these running for quite some time, I simply hooked it up to the load balancer and setup the necessary routing rules.
A few additional notes
I changed the LAN dhcp IP pool on my home router to 10.x.x.x/8 instead of the default 192.168.0.x/16 so that there would be no conflict when accesses resources in the home network from a remote network.
As my service provider does not offer static IPs, I had to run a docker container in my raspberry pi, which updates my public IP on the cloudflare A records periodically. The image that I am using on the container can be found here.
OpenVPN is configured for split tunneling such that any traffic other than those destined for 10.x.x.x/8 does not have to traverse through the VPN server and home network. This was done to improve the internet browsing experience on the remote devices. This is a security compromise that I am willing to take.
Where ever possible, the defaults settings such as ports were changed for improved security.
Finally, I’ve avoided minute details in this post for the sake of security and to keep the post less technical and lengthly.
Overall, it was a quick but fun project. I can now seamlessly and securely access all my files from any remote location. One day, if I have the need and the money, I might switch over to ubiquity hardware as I always wanted to try them out to set up a holistic home network with servers, IP cameras, virtual machine etc. I’ll perhaps write another post when that day arrives.